With this tool, you will no more need obsolete and unreliable Faraday baggage. You'll be able to clone original SIM card of the cellphone currently being investigated even without recognizing the PIN or make new SIM cards with any ICCID or simply just structure your SIM card to renew for the following use. You will also be capable to connect numerous SIM card readers simultaneously.
Of truth, present-day stability updates have made it more challenging for would-be criminals to use cloning. Fashionable chip cards are far harder to hack Because the info they carry is encrypted within the chip alone.
Reporting Strategies: Set up apparent methods for reporting suspected fraud. Be certain staff know whom to contact and what measures to take should they recognize a possible card cloning try.
The product or service was fantastic, and delivery was lightning-speedy! Customer care went over and further than to guarantee a clean getting practical experience. Undoubtedly ordering again from Discree t Cloned Cards!
Just before diving into RFID copiers, it’s essential to note that, for a house owner or manager, you do not want an entry Handle technique with qualifications that an RFID copier can duplicate.
Yes, critical fobs using RFID technological innovation may be cloned applying comparable equipment and approaches as proximity cards.
Our cloned cards are crafted with advanced technology, creating them undetectable and completely functional for buys, ATM withdrawals, and on line payments. Here’s all the things you have to know about buying cloned credit cards from Globalnotelab.
Update Software and Devices: Ensure that all software package, which include functioning devices and apps, is routinely current to the most up-to-date variations. Updates frequently include things like safety patches that tackle identified vulnerabilities.
When getting clone copyright, make sure the website you decide on makes use of strong encryption protocols to secure your personal and money facts. Encryption scrambles your information, which makes it unreadable to unauthorized events, furnishing A vital layer of defense towards cyber threats.
Suppose you see a sizable sum of money is missing from the account. Or Permit’s say your card statements include chargers or withdrawals at ATMs unknown to you personally.
Regardless of whether you’re upgrading an present technique or ranging from scratch, these items offer dependability and adaptability.
You may as well find this method under the name skimming, while phishing is when anyone falsely impersonates a respectable institution to acquire another person’s individual and financial institution information.
Start out by inserting the original device close to the reader card clone to extract its details. The reader will capture the power code and card amount, which are essential for cloning.
Rather, without the buyers, workers, or enterprise house owners becoming conscious of the supply of the breach, individuals accountable for the assault may perhaps simply Obtain knowledge on the constant foundation within the concealed scanners.
 Jennifer Grey Then & Now!
Jennifer Grey Then & Now!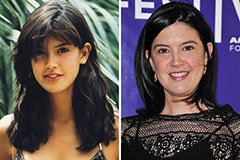 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Tonya Harding Then & Now!
Tonya Harding Then & Now! Lacey Chabert Then & Now!
Lacey Chabert Then & Now! Richard Dean Anderson Then & Now!
Richard Dean Anderson Then & Now!